Archive for May 2014
You Can Send Word Document as an Email to Easy Way.
Monday, May 26, 2014
Posted by Unknown
Tag :
Email
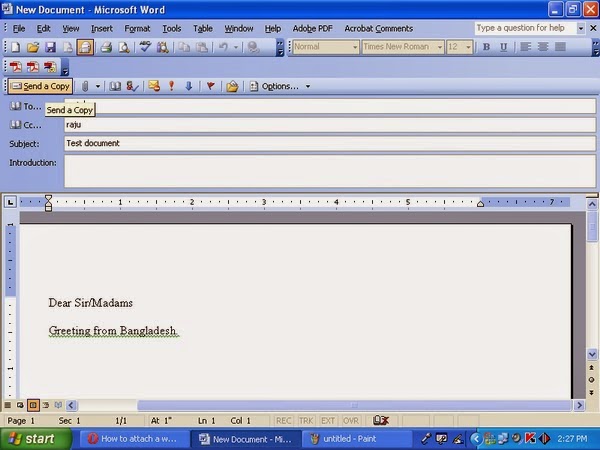
1. Open your word document type your topics and save it.
2. Click File on the menu bar.
3. Select send to - Mail Recipient.
4. Above your word document you should now see an email
tool bar that is full of
icons that you
are used to seeing in Outlook. Just fill it out as you would to send
any email.
5. When you are done filling address line and the SUBJECT click to
send your email.
Remember:
Your word document will be turned into an email automatically.
The recipients will not need to open it as an attachment or anything. The
size of the file will also be smaller which will help those who have full
mailboxes.
Microsoft Excel Most Important Shortcut Key
Wednesday, May 21, 2014
Posted by Unknown
Tag :
Ms Excel
Microsoft
Excel Most Important Shortcut Key
Excel
Shortcut Keys
|
Description
|
F2
|
Edit the
selected cell
|
F3
|
After
a name has
been created F3 will paste names.
|
F4
|
Repeat
last action. For example, if you changed the color of text in another cell
pressing F4 will change the text in cell to the same color.
|
F5
|
Go to a
specific cell. For example, C6.
|
F7
|
Spell
check selected text or document.
|
F11
|
Create chart from
selected data.
|
Ctrl +
Shift + ;
|
Enter
the current time.
|
Ctrl + ;
|
Enter
the current date.
|
Alt +
Shift + F1
|
Insert
New Worksheet.
|
Alt +
Enter
|
While
typing text in a cell pressing Alt + Enter will move to the next line
allowing for multiple lines of text in one cell.
|
Shift +
F3
|
Open the
Excel formula window.
|
Shift +
F5
|
Bring up
search box.
|
Ctrl + 1
|
Open the
Format Cells window.
|
Ctrl + A
|
Select
all contents of the worksheet.
|
Ctrl + B
|
Bold
highlighted selection.
|
Ctrl + Z
|
Undo
last action.
|
Ctrl +
F3
|
Open
Excel Name
Manager.
|
Ctrl +
F9
|
Minimize current
window.
|
Ctrl +
F10
|
Maximize currently
selected window.
|
Ctrl +
F6
|
Switch
between open workbooks or windows.
|
The terms bit and byte are same in
computer networking. Both terms refer to digital data transmitted over a
network connection. Bits and bytes both may represent network addresses or port
numbers.
Bit: A bit is a single numeric value, either '1' or ‘0’ that encodes a
single unit of digital information.
Byte:
A byte is a sequence of bits; usually eight bits equal one
byte.
Cloud Computing:
Thus your computer has died .
Your external hard drive was stolen from your car. Then your house burned down. By all rights, you’re having a total fail
of an afternoon. But by backing up your computer’s data to the cloud, none of
these traged ies need cost you your precious memories. cloud storage Simply, backing up data to the cloud means you’re backing
up data to our secure servers via your Internet connection, instead of just to
a hard drive in your home or office. Using cloud backups, you’ve removed from your shoulders the burden and stress of
protecting whatever device your data is stored
on.
Protecting data on lost laptops with encryption:
Laptops are easily lost or stolen. It’s embarrassing for
the person who has left the laptop in the back of the car, or let it out of
their sight at a conference or in the airport. It’s more than embarrassing for
your company however. Laptop loss or theft presents a real danger of serious data
breach, leading to security and compliance problems.
Any time any person lost a laptop while traveling. It
contained the personal data of
thousands of compensation claimants. The data included
names, phone numbers, add resses and
social security numbers. The laptop was password protected
but the information wasn’t encrypted .
This huge case highlights the need
for all confidential data to be properly and appropriately protected . Whether a laptop is lost, stolen as a crime of
opportunity, or targeted by a thief
who has specific knowled ge of your
business, the result is the same. The laptop has gone, and everything contained on it is beyond your control, and vulnerable to
abuse.
Password protection alone is not enough to protect your
data. The worst case is that there’s a Post-It note stuck on the laptop with
the password written on it. It may be that a default password is being used by more than one employee. Even a unique password
can be bypassed , because it is data
on the disk drive like everything else. If the data is not protected , neither is the password, and it can be accessed easily.
Security of data is not the only risk faced when a laptop goes missing. Compliance issues are
raised when considering potential
effects of data breaches through loss or theft. The Data Protection Act,
industry regulations such as the Payment Card Data Security Standard (PCI DSS)
and ISO 27001 require information to be kept safe and secure. A laptop
containing data that can be easily accessed
by an unauthorized user is neither
safe nor secure.
Encryption protects all your data. Once encrypted , only those who are authorized can access it. The password is part of the
encrypted data, and can’t be
discovered by someone who doesn’t
know it. Your data remains safe even if your laptop is stolen or goes missing.
Effective encryption solutions can be found in Sophos
Safeguard products. Full-disk encryption protects all confidential and
sensitive data on desktops, laptops and removable med ia.
It allows authorized users to share
data securely, easily and fast. Detailed
logs, along with compliance reports on users and encrypted
devices keep you informed . With
Sophos Safeguard you can prevent data breaches, comply with regulations, and
ensure security and data protection is up to date. Human error will always mean
that laptops are lost or left vulnerable to theft.
1. Image select mouse right click with ACD Photo Enhance.
IT Tips:
1. Do not use android
mobile/smart phone while charging.
2. Do not answer any calls
or call out while charging your android
mobile/smart phone.
3. Please alert about
using UPS backup and electric power line via
power strip
4. When cleaning a
component (specially keyboard) of Laptop or
desktop, turn it off before cleaning.
5. Never spray any liquid
onto the Laptop component.